

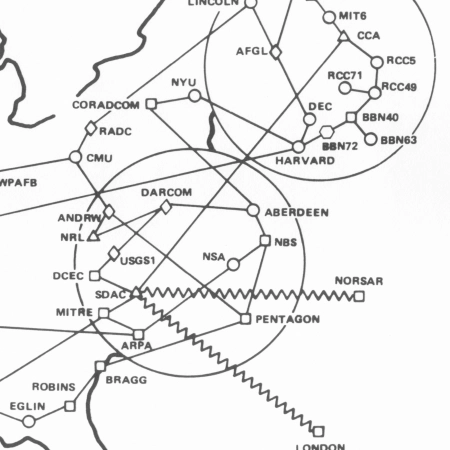
ARPANET Maps

Breaking Bitlocker

Play the Password Game!

Leaking Secrets Under Social Pressure

GPT and Confirmation Bias

SCI//HCS-P/SI/TK at Mar-a-Lago

The Mar-a-Lago Mess
The Quantum Computer Bogeyman

Can I auto-post to Mastodon?

Mastodon

Writing Nonfiction with ADHD

Telepathic Declassification

Email Attack via a Recycled Domain

Cybersecurity for MSSE 2023

Update: Tweeting Top Secret
Online Course: Cloud Top Ten Risks

Cybersecurity for MSSE 2022
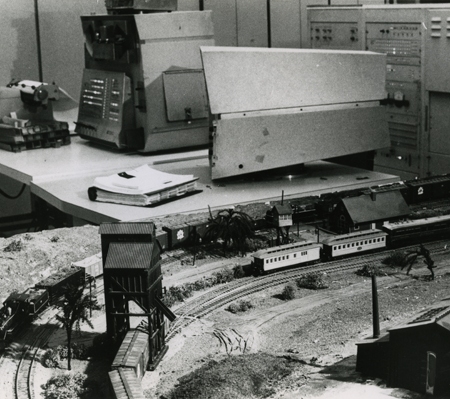
PDP 1s and Model Trains

Cities, Disneyland, and Software Security

libhairshirt vs libfootgun

Cloud Security Specialization Launched
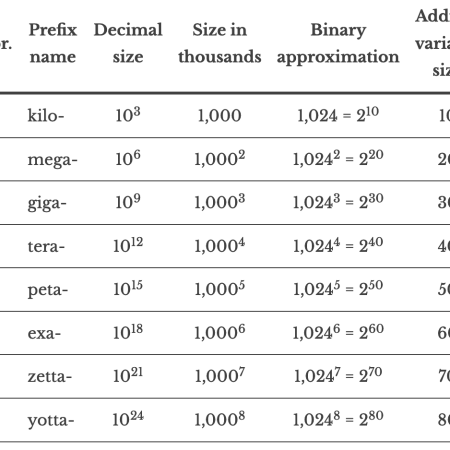
Memory Sizes: Now with zetta and yotta!

Selling It: Crypto Edition


You must be logged in to post a comment.