Favorite Posts
Memory Sizes: kilo mega giga tera peta exaOctober 18, 2013
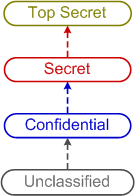
SCI//HCS-P/SI/TK at Mar-a-LagoJune 4, 2023
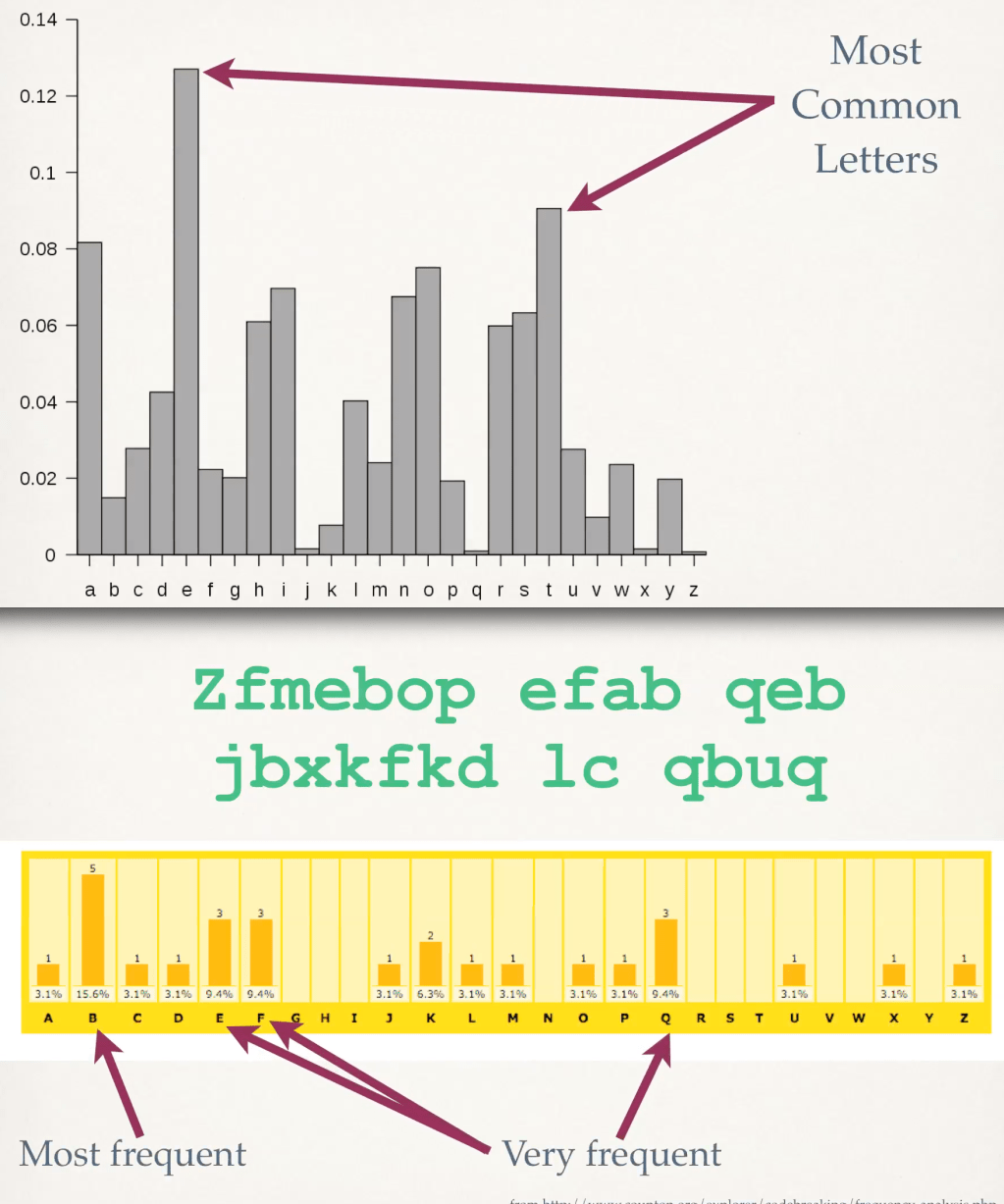
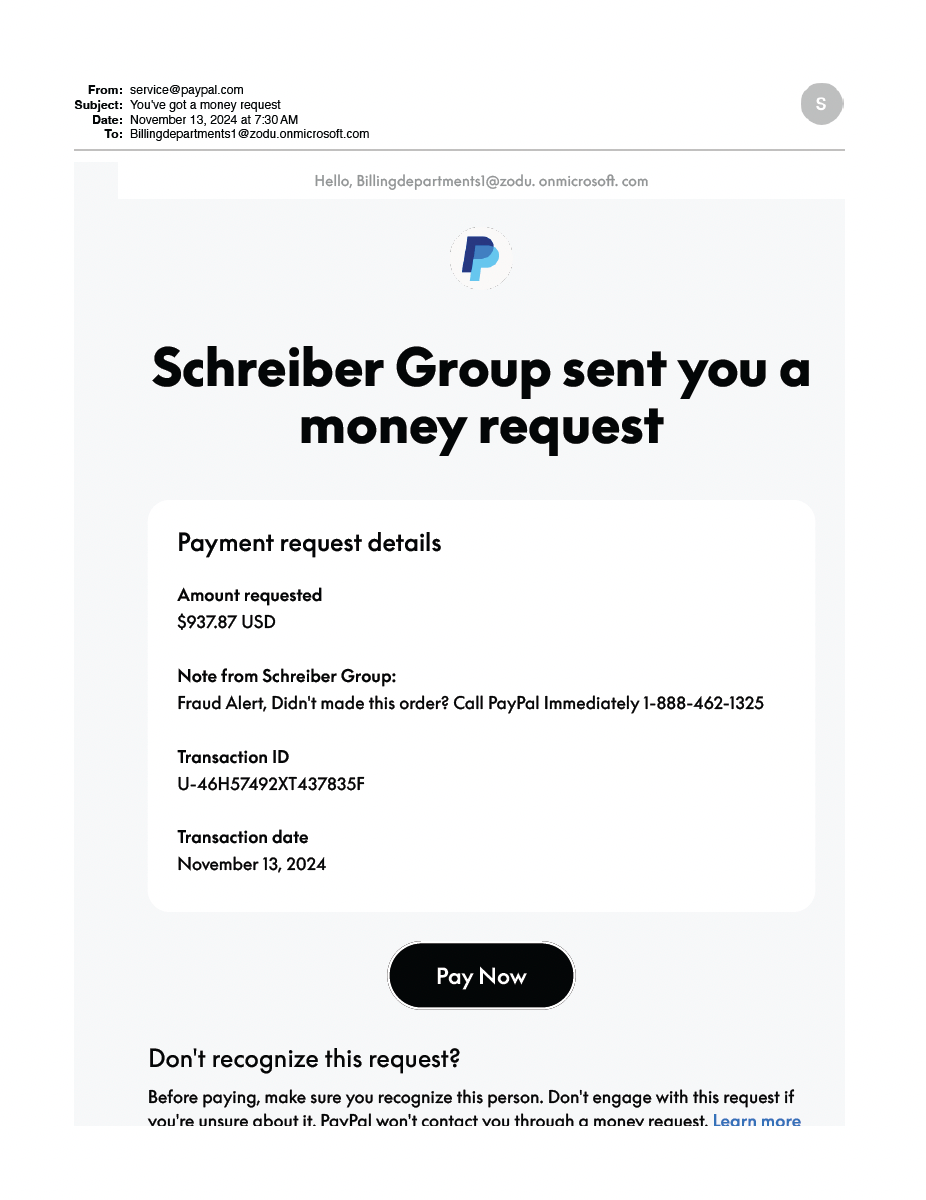
Password Hashing and CrackingMarch 26, 2021
Kilo mega giga teraOctober 19, 2013
Password SanityOctober 20, 2014
Stream Cipher Reuse: A Graphic ExampleMay 31, 2008
ACSAC Android Apple attacks authentication Bitcoin Boak Calibre certificates CIA properties classified Clinton cloud computing Coursera CPU cracking crypto cybercurrency databases design principles domain names Drupal ebooks elections email encrypted messages evaluations file systems flaws Ft. Meade GUI history iOS iPhone KGB Kindle library malware memory sizes Microsoft mobile security MSSE Multics NSA NSTISSI 4011 OPDS passwords phishing President quantum Quizlet RAM risks secrecy spam SSL stream cipher TCSEC Top Secret training Trump UMN video Wordpress xor