crypto
-
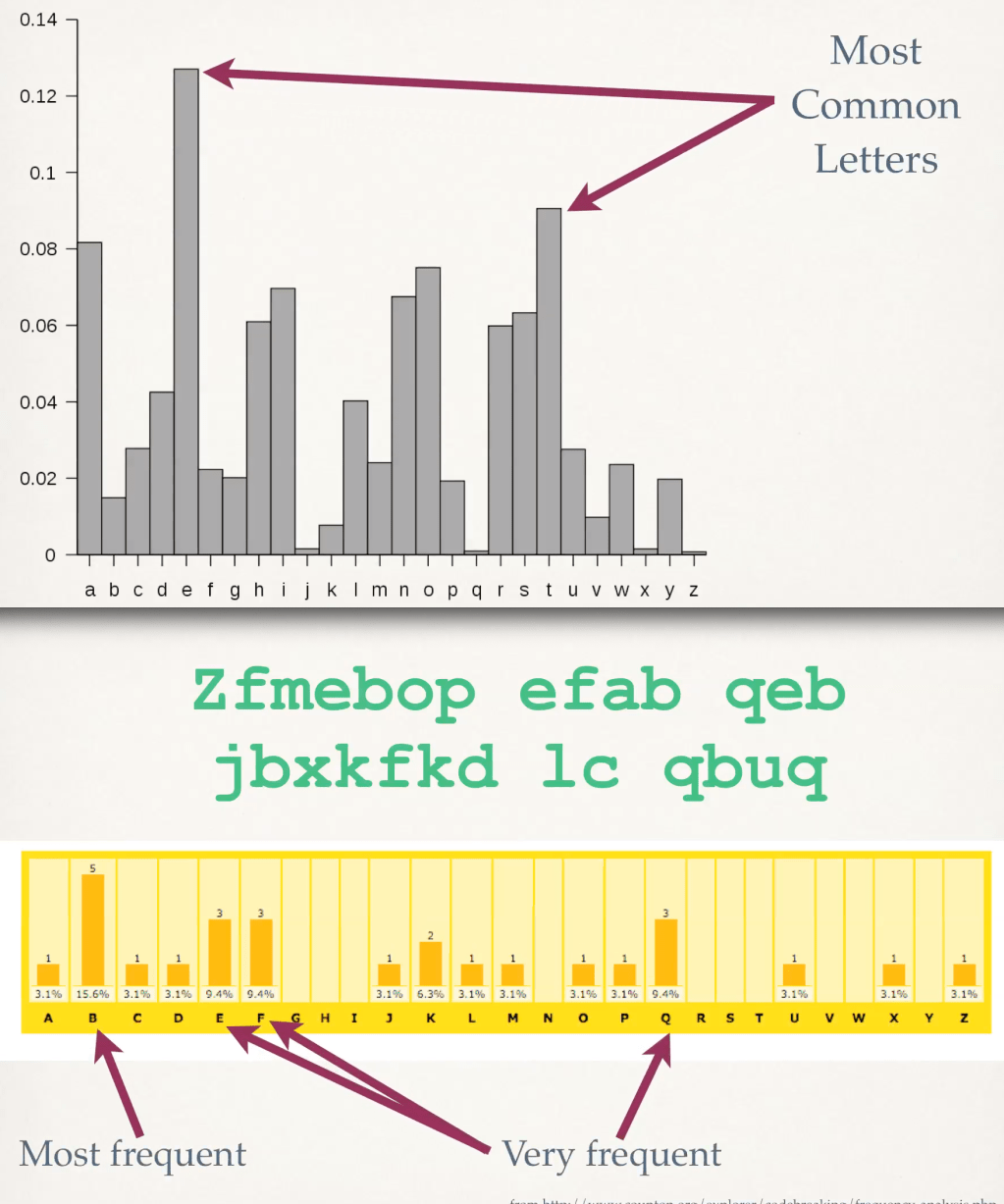
Making Fun of Quantum Codebreaking
Quantum codebreaking uses a theoretically “large” quantum computer to break secret codes. Today, quantum computers handle…
-

Breaking Bitlocker
It was only a matter of time before someone did this. Bitlocker is Microsoft’s technique for…
-
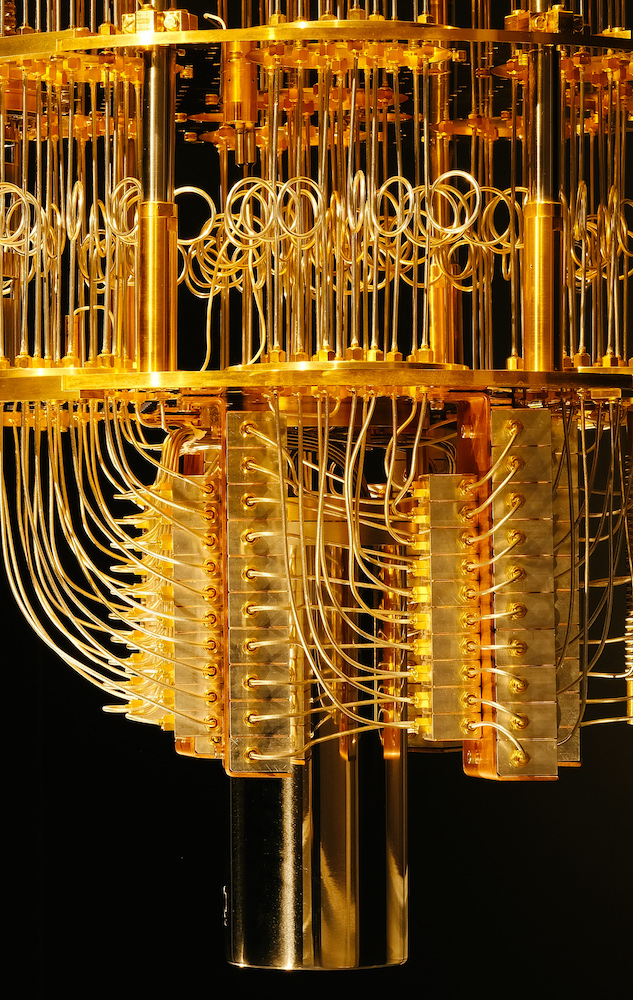
The Quantum Computer Bogeyman
Peter Gutmann of the University of Aukland recently published a parable “On the Heffalump Threat.” He…
-

libhairshirt vs libfootgun
Peter Gutmann, an interesting crypto-academic from New Zealand, has proposed discussing two crypto libraries, libhairshirt and…
-
Selling It: Crypto Edition
Here is a crypto version of “Selling It,” a long-running back-page column in the magazine Consumer…
-
WPA2 Packet Frame Format
Wireless Protected Access, Version 2 (WPA2) is the version of Wi-Fi security used in most cases…
-

Sen. John McCain, 1936-2018
In June, 1999, Senator John McCain had started his presidential bid and was visiting companies in…
-

The Six Types of Cyber-Risks
My textbook lists categories of cyber-attacks that focus on an attack’s lasting impact: how does it affect the…
-
Quantum Skepticism
Quantum computing gives us a way in theory to quickly crack certain types of cryptography. Well-funded…
-
The Big Bug in the News: the WPA2 flaw
The big news this week is a protocol flaw in the Wireless Protected Access protocol, version…
-
Tiptoeing Through Vulnerabilities
I sympathize with developers who throw up their hands and say, “I don’t do security stuff.”…
-
Cryptosmith Video Series
I have posted the fifteenth video in the Cryptosmith Series on practical basic cryptography. These videos use animation…
-
How DVD Crypto Keys Work
Here are a couple of short videos that describe the basic cryptographic mechanisms used in DVDs.…
-
Cryptosmith Video Series
The Cryptosmith video series uses animation to explain well-known crypto techniques. This should help more people…
-
Election Crypto Conspiracy Theory
I’m not often a fan of conspiracy theories, except for entertainment value. This one is interesting…
-
A Yank at Bletchley Park
A friend and colleague introduced me to a 94-year-old gentleman with a rare tale to tell. John…
-
Symantec Breaks Trust with the Internet?
Symantec is one of the companies that holds the keys to the Internet: they are a trusted…
-
The Apple case isn’t “privacy” versus “safety”
The current fight is about whether we will impose a technological infrastructure which will be exceptionally…
-
Backing Up OS X with Mirrored Encrypted RAID
Computing technology is insanely reliable when you look at statistical error rates. Hard drives read and…
-
NSA re-releases Boak’s Lectures
I’m a fan of Boak’s Lectures – they cover the fundamentals of military cryptography just before…
-
Recycling an iPhone – not a picnic
I’m upgrading my iPhone and trading in the old one. I had to erase the old one completely…
-
Encrypt All Hard Drives!
If you have the technical interest to read this, you probably do a lot of your…


You must be logged in to post a comment.