It was only a matter of time before someone did this. Bitlocker is Microsoft’s technique for encrypting a desktop, laptop, or other MS Windows device. We encrypt the device to protect the contents if it is ever stolen. In theory, the only way Windows will start up if it is Bitlocked (is that really a word?) is by entering the right password when it boots.
A researcher who uses the name stacksmashing has posted a Youtube video showing how to decrypt a Bitlocker-encrypted hard drive on a Lenovo laptop. The process requires a special $10 part for which stacksmashing provides many construction details. The documentation notes that this is an experiment, and does not really provide a “professional or production device.” Still, it’s good enough for knowledgeable people to build and use it themselves.
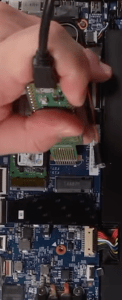
The process is not for the faint of heart, even if someone builds a “TPMSniffer” (the custom $10 part) for you. You need two separate computers: one to host the sniffer and provide text I/O, and the “target” Lenovo laptop whose Bitlocker you are trying to decrypt.
- Plug the TPMSniffer into the host’s USB port.
- Run software on the host to display text sent back by the TPMSniffer
- Turn off the target laptop
- Take the back off of the target laptop
- Place the probes on the TPMSniffer on the “Debug Port” on the target laptop’s motherboard.
- Power up the target computer.
- Host computer will display the target’s Bitlocker encryption key.
- Copy the key.
- Turn off the target computer.
- Disconnect the system drive from the target laptop
- Connect the target system drive to a computer that has Bitlocker unlocking software, like “dislocker” on Linux.
- Run the unlocking software and provide the target’s Bitlocker encryption key.
- Read and write the target’s system drive.
Thirteen steps. How appropriate.
Why it Works
Hack-resistant crypto hardware is incredibly hard to build. I’ve written about this in my various books. The standard reference is Ross Anderson’s Security Engineering, which is available entirely online in its older editions. Don’t worry: it’s still worthwhile to look at the earlier editions, since people continue to make the same old mistakes.
Most mobile devices, especially smartphones, are designed to resist attacks that use programmable electronic probes. The usual defense is to embed as much of the logic as possible in silicon, since it’s impractical for most attackers to extract data from inside a monolithic silicon device. We don’t want a device to transmit cryptographic keys between monolithic devices because the wiring between them yields a way to extract such keys.
This is exactly the problem being exploited here. Lenovo laptops use a Trusted Platform Module (TPM) to protect cryptographic keys. The laptops encrypt and decrypt the system drive using cryptographic software in the CPU. Lenovo uses separate silicon devices for the TPM and the CPU, and the TPMSniffer intercepts the signals between the two. When the CPU asks for the Bitlocker key, the TPM sends it back in plaintext, that is, without encryption.
Note for experts: it’s technically possible to implement encryption between the TPM and CPU to protect the Bitlocker key and other sensitive data. It takes a lot of careful design and engineering. The extra work makes the system more complex and opens the risk of introducing other weaknesses.
The Register posted a good article on this.

Responses
https://en.wikipedia.org/wiki/As_Tears_Go_By_(song) provides a platform to launch an alternate lyric: “I sit and watch [the bus] as keys go by…”
LikeLiked by 1 person
[…] *** This is a Security Bloggers Network syndicated blog from Cryptosmith authored by Rick. Read the original post at: https://cryptosmith.com/2024/02/12/breaking-bitlocker/ […]
LikeLike
[…] *** This is a Security Bloggers Network syndicated blog from Cryptosmith authored by Rick. Read the original post at: https://cryptosmith.com/2024/02/12/breaking-bitlocker/ […]
LikeLike