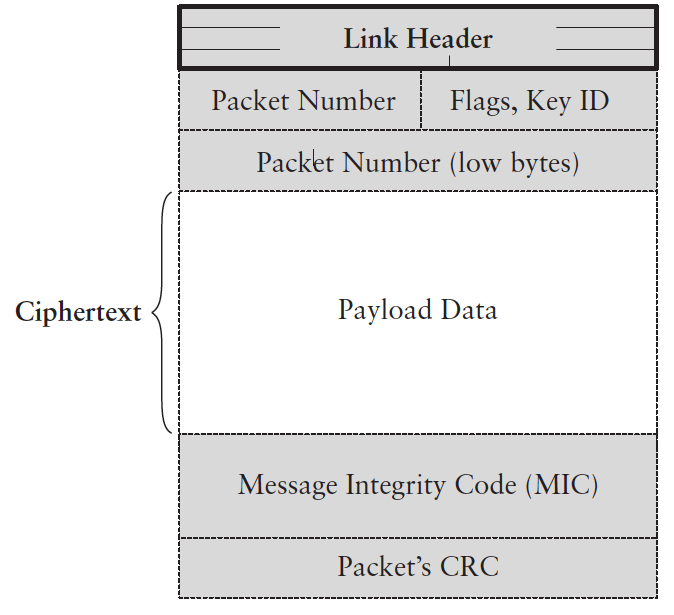
Wireless Protected Access, Version 2 (WPA2) is the version of Wi-Fi security used in most cases today. This diagram illustrates the general layout of the security data used by WPA2. There’s a new version coming out, WPA3, but it doesn’t seem to be in any products yet.
I put this diagram together several years ago for my textbook. I recently performed a web search for similar diagrams only to realize that there aren’t any posted.
Here is an explanation of the packet’s contents:
- Link Header: the IEEE 802 header for the Wi-Fi packet, including the payload but excluding the packet’s CRC.
- Packet Number: each packet is individually numbered so that the recipient can detect duplicate packets. The Wi-Fi retransmission protocol makes it possible, even likely, that individual packets will occasionally arrive in duplicate. The whole packet number is six octets (bytes) long, with the lower 4 bytes appearing after the Flags and Key ID.
- Flags and KeyID: There are two bytes reserved in the header for flags and the KeyID.
- ExtIV Flag: This is the only flag; it indicates that this header contains 8 bytes instead of the 4 bytes used in the now-obsolete Wired Equivalent Privacy (WEP) crypto protocol.
- KeyID: Selects one of four keys established for this conversation.
- Payload data: the packet’s data contents, including protocol headers for Layers 3 through 7. Encryption is with CCM mode as described in RFC 3610.
- Message Integrity Code (MIC): The code is calculated as described in the CCM mode noted above. The calculation uses CBC-MAC to calculate the MIC. The “encrypted” curly brace should probably include this field. If I read the RFC correctly, the MIC is essentially double encrypted.
- Packet’s CRC: The error-detecting cyclic redundancy check, calculated as stated in the IEEE 802 standard.
The source of this information is the IEEE Standard 802.11-2007, which was the version I extracted when I first produced this figure. The latest version is dated 2016, but I haven’t managed to download it yet, and check it against this diagram.

You must be logged in to post a comment.