phishing
-

Another Telephone Phish
A person called me on the phone a few moments ago claiming to be from US…
-

Assessing an Email’s Legitimacy
I recently received an email sporting “Wells Fargo” logos. It asked me to do a survey.…
-
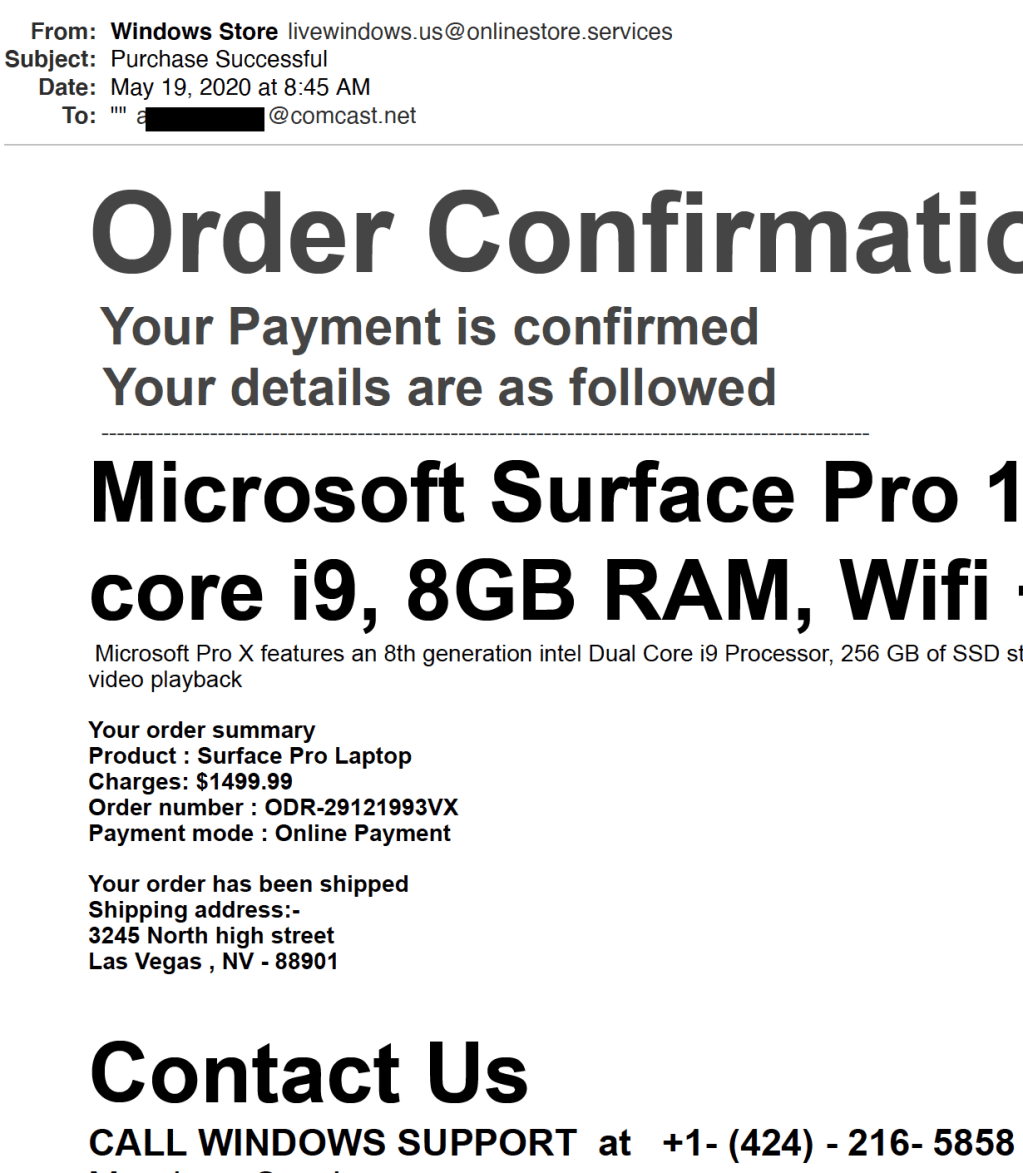
Beware of Phone Phishing
Just because the email (or letter) directs you to a phone number doesn’t mean you aren’t…
-
Detecting a Phish on an iPhone
In their obsession with simplifying the phone interface, the iPhone designers make it a bit harder…
-
Rule #1 for Detecting a Phish
Golly. This one was really hard to spot. Just kidding. This is obviously a fake email.…
-
A Mac Hack
Here’s a clever two-step attack on a Macintosh. First, the victim downloads a file – it…
-
Invoice Phishing Campaign
Here is a phishing email I received today. These almost always land in my junk mail…
-
Interesting Email Scam I Received
I received an impressive email scam recently. My response was to forward it to the email…
-
How to Trace an Email Message
There is no way to verify an email’s contents except through cryptography. Until every email client…
-
HR and Phishing
I receive thousands of emails every month. I do a lot of (for me) critical activities…
-
University: Anti-phishing not really a “policy”
UMN will never ask for personal info via email, except when they can’t help it.
-
My invitated – a classic phishing attack
Phishing emails can be tiresome. Sometimes, though, they are classically bad. Even better, this one uses…

You must be logged in to post a comment.