-

Another Telephone Phish
A person called me on the phone a few moments ago claiming to be from US…
-

Email Attack via a Recycled Domain
A software engineering friend fell victim to an almost-successful attack on his Facebook account. The attacker…
-

“Proud Boys” Emails Are Bogus
The Proud Boys emails aren’t actual threats. They’re the lowest form of anonymous spam.
-

Assessing an Email’s Legitimacy
I recently received an email sporting “Wells Fargo” logos. It asked me to do a survey.…
-
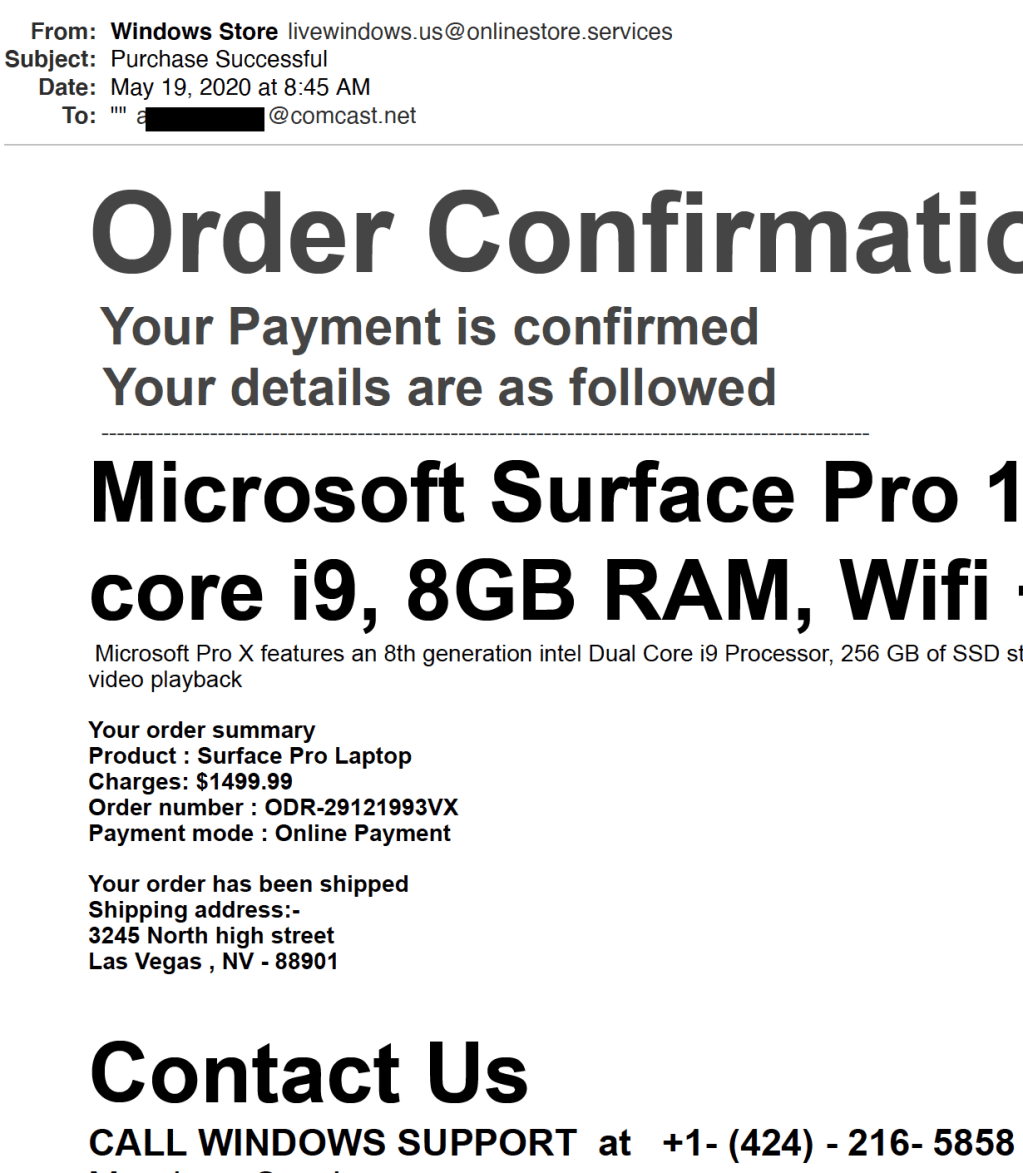
Beware of Phone Phishing
Just because the email (or letter) directs you to a phone number doesn’t mean you aren’t…
-
Detecting a Phish on an iPhone
In their obsession with simplifying the phone interface, the iPhone designers make it a bit harder…
-
A Forged “From” Address
To the left we see part of a malicious email. The author brags about how the…
-
Interesting Email Scam I Received
I received an impressive email scam recently. My response was to forward it to the email…
-
How to Trace an Email Message
There is no way to verify an email’s contents except through cryptography. Until every email client…
-
Comparing Leaks: Trump vs. Hillary
As I said in an earlier post, no crime is committed if the appropriate official leaks…
-
#PodestaEmails are NOT obvious fakes
Emails are notoriously hard to validate. Emails are like typed, signed contracts with no section or…
-
Election Crypto Conspiracy Theory
I’m not often a fan of conspiracy theories, except for entertainment value. This one is interesting…
-
Clinton’s Email Server Isn’t Her Scandal
Early last month, Edward Snowden criticized former Secretary of State Hillary Clinton for obviously and intentionally mishandling classified…
-
A Script to Generate Spam Comments
The text attached to this post was submitted as a web site comment. No doubt some…
Cryptosmith
Cyber and security architecture, not bitcoins

You must be logged in to post a comment.